Bob's Journey to Persistence: Keeping your Data Alive
Bob explores the world of Kubernetes Persistent Volumes and Claims, guided by Josie. Together, they tackle dynamic provisioning, securing connections to external services like PostgreSQL and MySQL, and best practices for resilience. Dive into this essential step in Bob's Kubernetes journey!

Bob, now comfortable with managing secrets and ConfigMaps, turned his attention to another crucial aspect of Kubernetes: persistent storage. He knew that containers were ephemeral, but what about data that needed to persist even if his pods were deleted or rescheduled?
"It's like my containers have amnesia," he thought, "but my data needs to have a long-term memory."
Josie, sensing his curiosity, approached with a smile. "Ready to explore the world of persistent volumes, Bob?" she asked.
Bob nodded eagerly. "I'm ready to ensure my data survives even if my pods don't."
📂 Code Repository: Explore the complete code and configurations for this article on GitHub.
Persistent Volumes
Josie explained that Persistent Volumes (PVs) were the solution to his data persistence needs. They provide a way to store data independently of pods, ensuring that data remains available even if the pods using it are terminated or rescheduled.
"Think of persistent volumes as external hard drives for your Kubernetes cluster," she explained. "They provide a reliable and persistent storage space for your applications."
Bob learned that PVs are created and managed by Kubernetes administrators and can be provisioned using various storage backends, such as cloud storage services, network file systems, and local disks.
Persistent Volume Claims
Josie then introduced the concept of Persistent Volume Claims (PVCs).
"PVCs are like requests for storage space," she explained. "They allow pods to claim a portion of a persistent volume for their use."
Bob learned that PVCs are created by developers and specify the desired storage capacity, access modes (read-only or read-write), and other storage requirements. Kubernetes then matches the PVC to a suitable PV, providing the requested storage to the pod.
Dynamic Provisioning with Storage Classes
Kubernetes supports dynamic provisioning through Storage Classes, which allow the cluster to automatically create PVs based on user-defined requirements. This eliminates the need to manually provision storage for each application.
For example, if Bob specifies a StorageClass in his PVC, Kubernetes dynamically provisions a PV that matches the criteria.
Josie explained, "Dynamic provisioning simplifies storage management by letting Kubernetes create Persistent Volumes automatically based on your application's needs. For dynamic workloads, StorageClasses automatically adjust to provide the exact storage needed, making it ideal for applications with fluctuating demands".
She demonstrated with an example of a StorageClass and a dynamically provisioned PVC:
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: fast-storage
provisioner: kubernetes.io/aws-ebs # Example provisioner for AWS
parameters:
type: gp2 # Example AWS EBS type
zones: us-west-1a # Availability zone
reclaimPolicy: Delete
"This StorageClass" Josie explained "tells Kubernetes to dynamically create storage using AWS Elastic Block Store with the gp2 type."
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: my-dynamic-pvc
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 10Gi
storageClassName: fast-storage
Josie continued, "When this PVC is applied, Kubernetes will automatically provision a 10Gi volume using the fast-storage class. It’s that simple!"
Bob nodded in appreciation, "This will save a lot of manual setup!"
Bob then realised that dynamic provisioning has a lot of benefits:
- Simplifies storage setup by automating volume creation
- Reduces manual errors and operational overhead
- Scales easily for applications with variable storage needs
Josie then says, "To see how everything connects, take a look at this diagram".
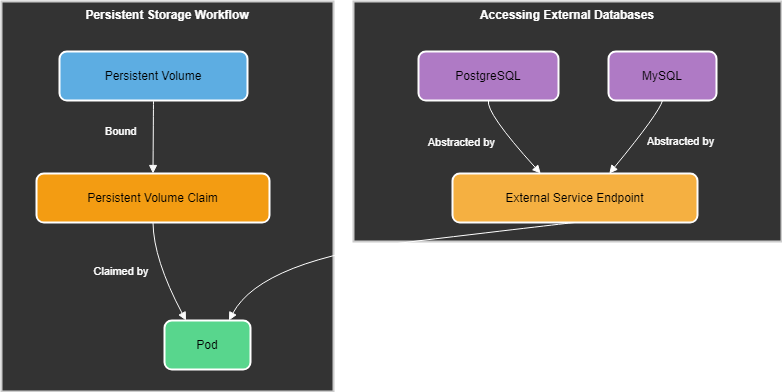
Accessing External Services
Josie then guided Bob on how to access external services like PostgreSQL or MySQL from his Kubernetes deployments.
"External services are like neighbouring buildings in your Kubernetes city," she explained. "They provide specialised services that your applications can access."
Bob learned that external services could be accessed through their endpoints, which are essentially the addresses of the services. He also discovered that Kubernetes Services could be used to abstract the endpoints of external services, providing a stable and consistent way for pods to access them.
While connecting to external databases like PostgreSQL or MySQL, it's crucial to secure these connections by:
- Using Secrets for credentials
- Restricting access through firewall rules or network policies
- Monitoring connections for suspicious activity
- Ensure connectivity leverages TLS
Josie explained, "Abstracting external service endpoints with Kubernetes Services provides several key benefits. It creates a stable, consistent interface between your pods and the services they rely on."
She elaborated on the benefits:
- Portability: "Your pods don’t need to know the IP or DNS of the actual service. If the external endpoint changes, you only update the Kubernetes Service, not every pod"
- Resilience: "Decoupling your pods from the endpoint protects you from disruptions. If the external service changes or has issues, the abstraction layer shields your apps"
- Centralised Management: "Services also help streamline configurations for load balancing, network policies, and TLS"
Bob nodded. "So, it's like creating a directory listing that always has the latest office address. My pods just follow the directory instead of memorising the route."
"Exactly!" Josie said with a smile.
Best Practices for Connecting External Services
Bob looked thoughtful. “What’s the best way to connect securely to these services?”
Josie listed a few strategies:
- Use Secrets for Credentials - "Store sensitive data like database credentials in Kubernetes Secrets, not directly in your pod specs."
- Encrypt Connections - "Always enable TLS to prevent data interception. It's like sealing an envelope before mailing it"
- Apply Network Policies - "Use Network Policies to limit which pods can access your external services. Think of it as granting access only to your team members"
- Monitor and Retry - "Configure health checks and retries to handle external service hiccups. No one likes a dropped call!"
Bob grinned, "Sounds like I’ll need a combination of security and resilience to get this right"
Josie nodded. "Exactly. Let’s summarise with some key takeaways"
- Abstract external services with Kubernetes Services for portability and resilience
- Store credentials securely in Secrets and always use encryption for connections
- Apply Network Policies to control pod-to-service traffic
- Monitor endpoints and configure retries to minimise downtime
Connecting to PostgreSQL
Josie then showed Bob how to connect his application to an external PostgreSQL database.
"You'll need to create a Service that points to the PostgreSQL endpoint," she explained.
They crafted the following YAML definition:
apiVersion: v1
kind: Service
metadata:
name: my-postgresql-service
spec:
type: ExternalName
externalName: my-postgresql.example.com
"This Service acts as a bridge to your PostgreSQL database," Josie explained. "Your pods can then access the database through this Service."
Bob nodded, appreciating the simplicity and elegance of the solution.
Connecting to MySQL
Josie then showed Bob how to connect his application to an external MySQL database.
"The process is similar to PostgreSQL," she explained. "You'll create a Service that points to the MySQL endpoint."
They crafted the following YAML definition:
apiVersion: v1
kind: Service
metadata:
name: my-mysql-service
spec:
type: ExternalName
externalName: my-mysql.example.com
"This Service provides a consistent way for your pods to access the MySQL database," Josie concluded.
Bob was grateful for Josie's guidance on persistent volumes and external services. He now understood how to manage persistent data and connect his applications to essential services like PostgreSQL and MySQL.
As Bob continued his Kubernetes journey, he felt more confident in his ability to build and deploy resilient and stateful applications. He knew that persistent storage and external services were crucial components of the Kubernetes ecosystem and that understanding them was essential for mastering Kubernetes deployments.
Turning to Bob, Josie saying "Bob, you've mastered persistence and connectivity, but now it's time to tackle an even bigger challenge: exposing your applications to the world ... securely. Let's dive into ingress controllers and certificates."
