Trivy: A Developer's Guide to Keeping Your Apps Safe (and Your Sanity Intact)
Explore how Trivy simplifies security scanning across your development lifecycle. From source code and Docker images to Helm charts and Kubernetes clusters, this guide dives into practical ways to integrate Trivy and enhance your app’s security without the overhead.

Alright, let's face it, we've all heard the saying, "Being hacked is inevitable; it's only a matter of when you become interesting." But that doesn't mean we should just throw our hands up and wait for the inevitable! Instead, let's be proactive and use the tools at our disposal to keep our applications safe. That's where Trivy comes in... it's like having a security guard for your applications, images, and configurations, making sure everything is locked down tight.
What's the Deal with Trivy?
Trivy is an open-source vulnerability scanner from Aqua Security. It's designed to be easy to use and can be integrated into various stages of your development process. Think of it as your security sidekick, always there to help you catch those pesky vulnerabilities before they turn into major headaches.
Why Should You Care About Trivy?
- Shift-Left Security: Find and fix vulnerabilities early in the development cycle, so you don't have to deal with them later when they're harder to squash
- Fast Feedback Loops: Get immediate feedback on security issues during development, so you can fix them before they become a bigger problem
- Easy Integration: Trivy plays nicely with your CI/CD pipelines, IDEs, and container registries. It's like a chameleon, blending seamlessly into your existing workflow
- Comprehensive Scanning: Trivy covers a wide range of vulnerabilities, including OS packages, language-specific packages, misconfigurations, and even those sneaky secrets lurking in your code
But how can you leverage Trivy effectively in your specific role? Let's dive in and explore how Trivy can help you secure your applications, no matter where you fit in the development process. The diagram below illustrates Trivy's role as the central hub for securing various stages of the application lifecycle.
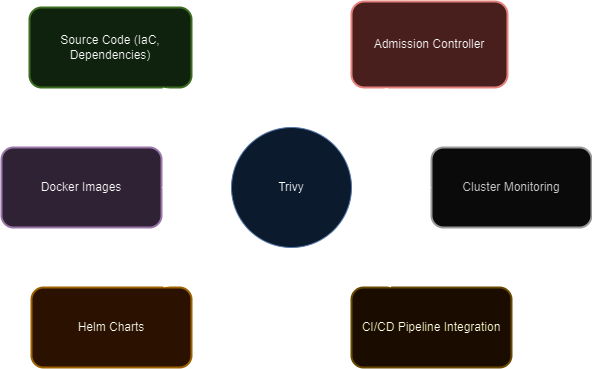
As an app developer...
As a developer, you're the first line of defence against vulnerabilities. Trivy equips you to catch security issues early on, right in your local environment. You can use Trivy to scan your project directory for any vulnerabilities in your dependencies. It can also uncover those pesky secrets that might have accidentally made their way into your code. Think of it as having a security expert do a quick code review for you!
As example, here's the scan results for a clean ReactJS install:
$ trivy fs my-example-app
2024-11-17T16:20:06Z INFO [vuln] Vulnerability scanning is enabled
2024-11-17T16:20:06Z INFO [secret] Secret scanning is enabled
2024-11-17T16:20:06Z INFO [secret] If your scanning is slow, please try '--scanners vuln' to disable secret scanning
2024-11-17T16:20:06Z INFO [secret] Please see also https://aquasecurity.github.io/trivy/v0.56/docs/scanner/secret#recommendation for faster secret detection
2024-11-17T16:20:06Z INFO Number of language-specific files num=1
2024-11-17T16:20:06Z INFO [npm] Detecting vulnerabilities...
package-lock.json (npm)
Total: 2 (UNKNOWN: 0, LOW: 0, MEDIUM: 1, HIGH: 1, CRITICAL: 0)As you can see, even a clean deployment of a ReactJS app using npmx create-react-app my-example-app has vulnerabilities in. Fixing most of these will be a case of running npm update or composer update if you are leveraging these technologies but the key is to catch them early and DON'T wait until deployment time!
For real-time feedback, you can integrate Trivy with your IDE. It'll act like a security-focused linter, helping you write secure code from the start. By finding and fixing vulnerabilities early on, you're shifting security left, making it an integral part of the development process instead of an afterthought. This proactive approach saves you time and headaches down the line.
For those rocking VS Code, "there's an extension for that"... basically, find it and click install and job done
Trivy identifies vulnerabilities in dependencies, allowing you to fix them before pushing your code to production
As an image builder...
When building images, it's important to scan the images for vulnerabilities not directly related to the code or it's dependencies such as those found in SSL libraries or core libraries like GlibC, Trivy provides a simple command for scanning these images locally or remotely:
$ trivy image my-example-app:1.0.0
2024-11-02T13:48:15Z INFO [vuln] Vulnerability scanning is enabled
2024-11-02T13:48:15Z INFO [secret] Secret scanning is enabled
2024-11-02T13:48:15Z INFO [secret] If your scanning is slow, please try '--scanners vuln' to disable secret scanning
2024-11-02T13:48:15Z INFO [secret] Please see also https://aquasecurity.github.io/trivy/v0.56/docs/scanner/secret#recommendation for faster secret detection
2024-11-02T13:48:17Z INFO Detected OS family="alpine" version="3.20.3"
2024-11-02T13:48:17Z INFO [alpine] Detecting vulnerabilities... os_version="3.20" repository="3.20" pkg_num=16
2024-11-02T13:48:17Z INFO Number of language-specific files num=1
2024-11-02T13:48:17Z INFO [node-pkg] Detecting vulnerabilities...
2024-11-02T13:48:17Z WARN Using severities from other vendors for some vulnerabilities. Read https://aquasecurity.github.io/trivy/v0.56/docs/scanner/vulnerability#severity-selection for details.
my-example-app:1.0.0 (alpine 3.20.3)
Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)Clean images mean fewer headaches down the pipeline
As a Helm deployer...
When you're packaging and deploying applications with Helm charts, it's essential to ensure those deployments are secure from the ground up. Trivy can help you examine your Helm charts for potential security misconfigurations before you deploy them, acting like a pre-flight checklist for your deployments.
You can use Trivy directly on your Helm chart directory:
$ trivy config my-example-app
2024-11-17T16:31:33Z INFO [misconfig] Misconfiguration scanning is enabled
2024-11-17T16:31:34Z INFO Detected config files num=3
templates/deployment.yaml (helm)
Tests: 93 (SUCCESSES: 79, FAILURES: 14, EXCEPTIONS: 0)
Failures: 14 (UNKNOWN: 0, LOW: 9, MEDIUM: 4, HIGH: 1, CRITICAL: 0)
For an even more thorough check, you can:
- Create the final Kubernetes YAML manifests produced by the dry-run command
helm install -f something . -f values --dry-run > manifest.yaml - Feed these manifests into Trivy for a detailed security analysis
This two-step approach ensures you're not missing any potential issues that might arise during the templating process.
$ helm install example-app . -f values.yaml --dry-run > example-app.yaml
$ trivy config example-app.yaml
2024-11-17T16:33:23Z INFO [misconfig] Misconfiguration scanning is enabled
2024-11-17T16:33:25Z INFO Detected config files num=1
example-app.yaml (kubernetes)
Tests: 122 (SUCCESSES: 94, FAILURES: 28, EXCEPTIONS: 0)
Failures: 28 (UNKNOWN: 0, LOW: 18, MEDIUM: 8, HIGH: 2, CRITICAL: 0)Running it on the dry-run output will convert all of your templates, secrets, configmaps etc. into a single file that can be used for both debugging and verifying the install and it allows you to scan the actual changes that are going to be made in your cluster when you deploy it.
Trivy is particularly good at catching common misconfigurations that can slip into Helm charts, such as:
- Missing Resource Limits: Trivy will point out if your deployments don't have limits set for resources like CPU and memory. Without these limits, your application could potentially consume excessive resources, impacting the stability of your cluster
- Privileged Containers: Running containers with excessive privileges is a security risk. Trivy will flag any instances where containers are granted more permissions than they need, helping you lock down your deployments
- Unrestricted Pod Access: Trivy can identify if your pods have unrestricted access to the host network or filesystem. This kind of access can be a significant security vulnerability, and Trivy helps you ensure your pods operate within safe boundaries
By addressing these issues early, you ensure your Kubernetes deployments follow best practices
As a Kubernetes Cluster Maintainer...
Kubernetes cluster maintainers have a big responsibility! You're the guardians of the cluster, making sure it's secure, stable, and running smoothly. Trivy provides the tools you need for continuous monitoring and protection.
One of your most powerful allies is the Trivy Operator. Deploying the Trivy Operator is like having a dedicated security watchdog that constantly patrols your cluster, automatically scanning your deployments and keeping an eye out for vulnerabilities.
But why wait for deployments to happen when you can prevent vulnerable images from entering your cluster in the first place? That's where Trivy's Admission Controller functionality comes in. It acts like a strict security guard at the gate of your cluster, carefully checking each image and turning away any that have known vulnerabilities.
And to stay ahead of the curve, Trivy provides continuous monitoring and alerts. This means you'll get notified promptly if any new vulnerabilities are discovered, allowing you to take immediate action and keep your cluster secure.
I'm not going to reinvent the wheel here but instead point you in the direction of their docs 🔗https://aquasecurity.github.io/trivy-operator/v0.22.0/
This being said, the following is an example admission controller that can be added to a cluster to prevent the deployment of vulnerable workloads:
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
name: trivy-admission-controller
webhooks:
- name: trivy-validator.k8s.io
rules:
- operations: ["CREATE"]
apiGroups: ["apps"]
resources: ["deployments"]
clientConfig:
service:
name: trivy-admission
This ensures that only secure workloads make it into your cluster
As a CICD Pipeline Maintainer...
For those managing CI/CD pipelines, ensuring that code changes are built, tested, and deployed securely and smoothly is a top priority. Trivy is designed to integrate seamlessly into your pipeline, automating security checks and making vulnerability detection a routine part of your workflow.
Think of Trivy as adding a crucial security checkpoint to your pipeline. With every code change or deployment, Trivy steps in to perform a thorough security assessment, scanning for vulnerabilities in your application code and Docker images.
Here's how you might incorporate Trivy into a typical pipeline stage:
trivy fs . # Scan the application code
trivy image my-image:latest # Scan the Docker image
trivy config . # scan the helm chart before deploying itTrivy is compatible with popular CI/CD tools like Jenkins, GitLab CI, and CircleCI, making it easy to integrate security scans into your existing workflows.
But it's not just about scanning; it's about taking action. Configure your pipeline to fail builds if Trivy detects vulnerabilities. This prevents insecure code from moving further down the pipeline and potentially being deployed.
As an example, github actions workflow could looks something like:
name: example-app-ci
on:
push:
branches: [ main ]
pull_request:
branches: [ main ]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Run Trivy vulnerability scanner in filesystem mode
uses: aquasecurity/trivy-action@master
with:
image-ref: '.'
format: 'table'
exit-code: '1'
# Fail the build if vulnerabilities are found
- name: Build the Docker image
run: docker build . --file Dockerfile --tag example-app:1.0.0
- name: Run Trivy vulnerability scanner in image mode
uses: aquasecurity/trivy-action@master
with:
image-ref: 'example-app:1.0.0'
format: 'table'
exit-code: '1'
# Fail the build if vulnerabilities are foundWhat this job basically does is checkout the code so it can be scanned, builds the example app docker image and scans it....; most importantly if either of these scans fail then it aborts the pipeline and no vulnerable deployments are made to your production clusters.
I'll let you figure out how to include the helm chart scanning into this workflow...
Integrating Trivy into your CI/CD pipelines ensures vulnerabilities are caught before they reach production
Wrap up
From experience, I've found that tools like Trivy aren’t about perfection... they're about visibility and control. It simplifies security, so you can focus on delivering value without second-guessing your foundations then you'll be quids in from the outset.
My key takeaways from writing this are as follows:
- Tools like Trivy integrate into existing workflows—whether it's a developer's local environment or a CI/CD pipeline—making security a natural part of the process rather than an afterthought
- By addressing different roles (developers, deployers, CI/CD maintainers), Trivy demonstrates its versatility, ensuring every stakeholder finds actionable value without needing to learn additional tools
- The earlier vulnerabilities or misconfigurations are caught (e.g., in code or Docker images), the fewer headaches arise later in production. Trivy simplifies this process by making results understandable and actionable
- Trivy stands out because it adapts to various stages of the development lifecycle—scanning source code, Docker images, Helm charts, or live workloads—without being intrusive
- This article isn’t about selling Trivy as a flawless solution but about sharing insights into how it simplifies a complex problem, helping teams focus on what matters: delivering secure, reliable applications
Security is an ongoing journey, not a destination. Remember to stay up-to-date with the latest Trivy features, keep its vulnerability database current, and follow security best practices to ensure your systems are always protected.
